Overview

Cybersecurity is the cornerstone of national security, corporate interests, and personal privacy.
With AI's rise, a cybersecurity solution must transcend traditional defenses to counter AI-driven cyber attacks, to ensure rock-solid data security and uncompromising regulatory compliance.
Security Solutions leverages intrinsic commercial cryptography, trusted computing, and confidential computing to deliver E2E security and industry-leading practices tailored for Internet, finance, foundation model providers, carriers, and public safety services.
Key Technologies
Commercial Cryptographic Application
Uses Kunpeng Security Computing Cryptographic Module (Kunpeng SCCM) to provide certified commercial cryptographic services, including algorithms, secure storage, and module management for diverse scenarios.
Trusted Computing
Enables a dual-system architecture compatible with worldwide standards and features high security and easy deployment.
Confidential Computing
Offers an innovative computing architecture powered by Kunpeng processors to safeguard the computing environment and and ensure data confidentiality and integrity for various industries.
Application Scenarios
Secure Cloud Host
Scenario
As services move to the cloud, data security faces challenges from malicious attacks, software vulnerabilities, and trust concerns regarding service providers.
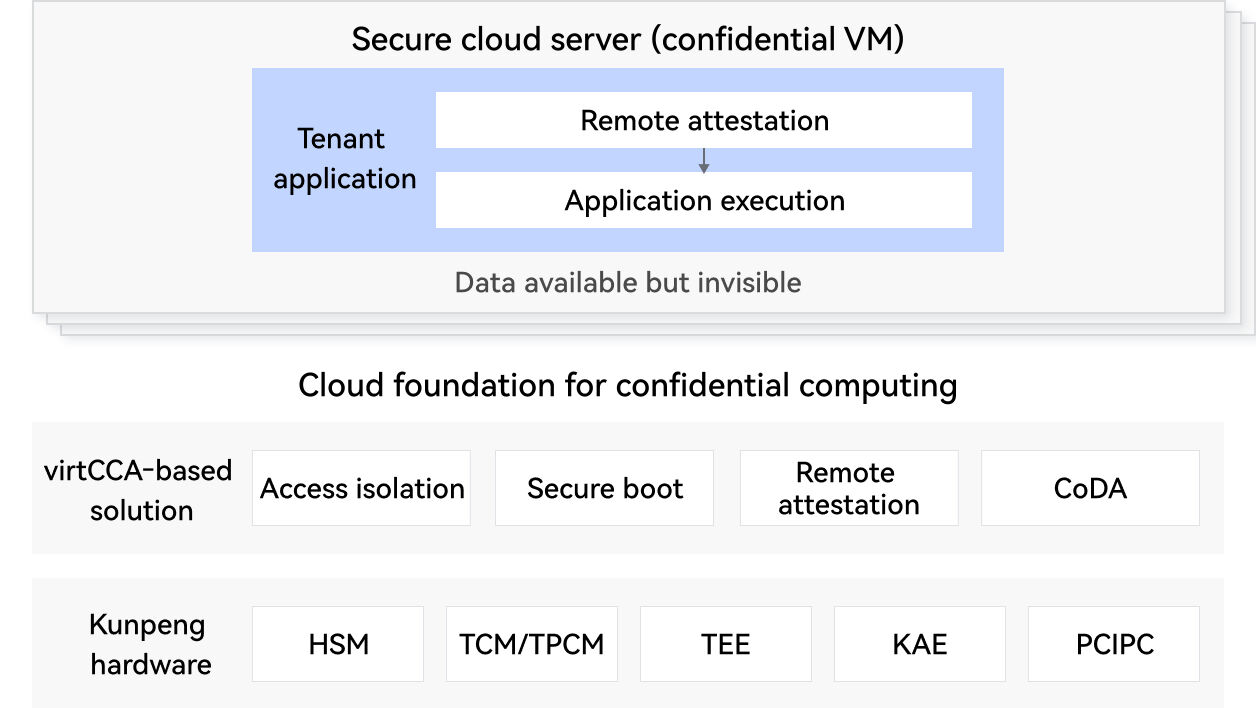
Cloud Foundation Solution for Confidential Computing
Computing isolation: virtCCA leverages chip-level hardware-enforced isolation to deliver secure computing resources, including bare metal servers, virtual machines (VMs), and containers.Trusted environment: Hardware Root of Trust (RoT) and remote attestation ensure that the entire IaaS environment is secure and verified.